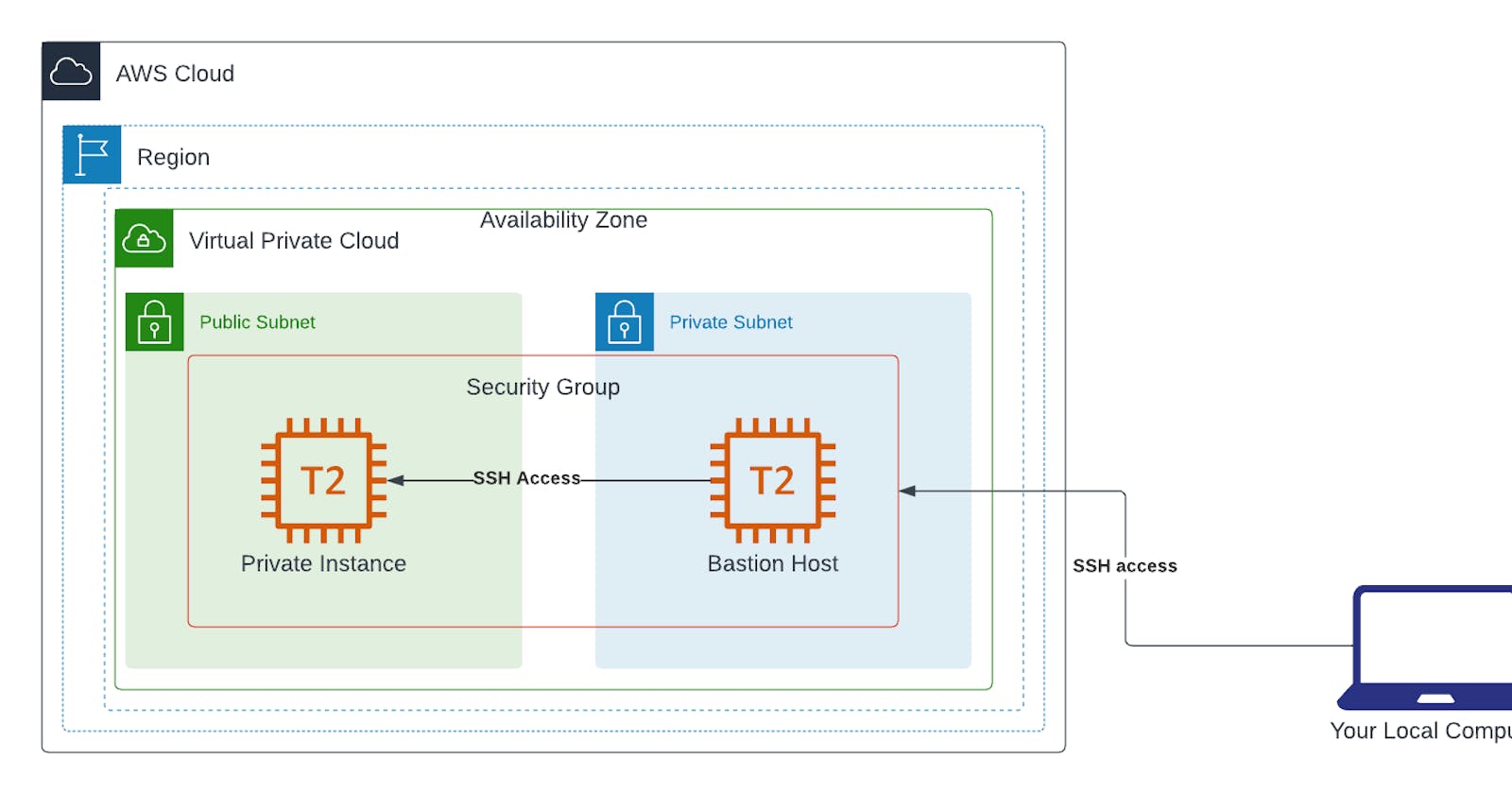
AWS Project: Architecting a Secure and Scalable Network with AWS VPCs and Subnets
After consistently focusing my time and attention mostly on writing articles that explore and examine theoretical cloud computing concepts I have decided to switch lanes and drive into Projects Boulevard (see what I did there?). Starting with this article, my focus is now on creating tutorial content by working on small AWS projects aimed at helping beginners and aspiring cloud professionals. In today's episode, (maybe I should have said today's edition since I'm writing right? But I hope you get the point regardless) the project we are going to work on configuring a custom VPC with a public and private subnet in the AWS cloud. After having done this, we are going to deploy a bastion host in the public subnet which will allow us SSH to an EC2 instance in the private subnet. The objective of this project is to help beginners understand concepts like VPCs, subnets, Network ACLs, routing, and security groups. Hope you are ready and excited because getting started right now.
Project Prerequisites
An AWS account that is free-tier eligible because we don't want to spend money on this project.
Basic knowledge of VPCs, subnets, Network ACLs, routing and security groups.
Grit. I had a deep conviction to include this because it is easy to give along the way when you hit a roadblock. I beckon you to still strive to complete the project regardless of any roadblocks that might ensue.
With the prerequisites out of the way, we can now start working on the project.
Step One: Creating a custom VPC and Subnets
The very first thing we have to do is to create our VPC. To do this, log into your AWS account to access the management console. Make sure you are not using the root user account to complete this project as you will not be following one of AWS's best practices which advises that we should avoid using the root user for everyday tasks like this one. Instead, it's recommended that you create an IAM user with administrative privileges and use it for this project.
Once you have logged into your IAM user account that has admin permissions, using the search bar of the management console, search 'VPC' and click on the first item in the search results that appear to open the VPC management console window as shown in the image below. If you feel the need to refresh your knowledge about VPCs, this article is the perfect resource for you.

For reference, I will launch all the resources I use in this project in the North Virginia region. If you want to follow along to the last detail, make sure you are also launching your resources in the North Virginia region.
Now let's create our VPC. Creating a VPC has been made easier as you can create your VPC and subnets, and define route tables and other VPC resources in one go.


Following the steps as indicated in the image above will enable you to create your VPC and its associated resources. Now let's move on the create a security group.
Step Two: Configuring Security Groups
To locate the security group console, we have to search and navigate to the EC2 management console window. Once in the EC2 dashboard navigate to the security groups tab and create a security group as shown in the image below.


Now that we have created the security group, let us go on to configure its inbound and outbound rules. In the inbound rules tab, click on Edit inbound rules and do the following: Search for the IP address of your computer by using this website and use it to create an inbound rule that allows SSH access to the resources that will be associated with the security group. The image below makes it easier to understand what I'm saying.

Using your IP address as the only allowed IP ensures that only your local machine (computer) with the specified IP address can establish SSH connections to the bastion host. This helps mitigate potential security risks by limiting access to your resources.
Step Three: Setting up a Bastion Host
The next step in the project is to launch a bastion host in the public subnet via which we are going to connect to an EC2 instance launched in the private subnet. So let's get that done. Within your management console, navigate to the EC2 window. To make sure we don't accrue any cost, we are going to use an AMI that is free-tier eligible.



While launching the EC2 instance, be sure to select the security group we created earlier as its security group. After having filled in all the details, clicking on the Launch instance button launches our bastion host EC2 instance. Now that it is up and running let's move on to the next step.
Step Four: Launch Private EC2 Instance
We need another EC2 instance in our private subnet which we are going to access it using SSH via the bastion host. This instance is going to use the same key pair and security group as the bastion host in the public subnet.
Step Five: SSH to Bastion Host
The time to start testing our work has come. We are going to access our bastion host from our computer. So open a terminal window and run the following commands.
chmod 400 /path/to/private/key.pem
This command will secure the key pair file that was downloaded when we created our key pair. After that, the next command to be run is:
ssh -i path/to/key.pem ec2-user@bastion-public-ip
Make sure you edit the command as needed before running it. With that, we will be connected to our bastion host and we can now connect to the private instance via SSH from the bastion host. To do that, run the following command:
ssh ec2-user@private-instance-private-ip
That's all that there is to it. Now close the connection to your EC2 instances by running the exit command.
Last Step
The very last step in this article is to clean up our resources because we wouldn't want to wake up to unwanted AWS bills right? So make sure you terminate the two EC2 instances we launched in this tutorial and delete the other resources as well.
Final Words
You've journeyed through the key aspects of AWS networks in this tutorial. You've learned about VPCs, bastion hosts, security groups, and the dynamic interplay of public and private subnets. These concepts might seem complex at first, but remember, they're the foundational blocks upon which secure and efficient AWS environments are built. So, as you continue to explore the AWS universe, know that you've laid the groundwork for creating safe, interconnected spaces for your applications to thrive. The skills you've gained here will serve as your compass as you navigate more intricate cloud landscapes. Keep building, keep learning, and may your future AWS ventures be as successful as your journey here. Happy networking!